Firefox has a relatively new feature called Containers. This feature allows users to create session containers, which means that it is possible for different sessions (i.e. cookies) to exist in different tabs or windows. This is rather useful for general privacy but I’ve found it can be immensely useful for web application testing too, as it helps significantly with testing access control issues – being able to switch between sessions between tabs Previously this was only possible using private windows, or different browsers, but now there is a simple and convenient plugin that can be used – Multi Account Containers.
However, this plugin only goes so far – and my process using it involved me manually adding cookies on each session and then using the Burp Plugin Request Highlighter to highlight all requests using this cookie. Whilst this approach worked, it was time consuming and fiddly.
I recently discovered a tool by @Bitk, specifically designed to solve this, called ‘Pwnfox’. It creates coloured sessions on the browser side, and through a Burp plugin automatically colours all requests from that session. This makes testing access control issues much less frustrating, and I highly recommend using it.

Going one step further with Containers, I’ve found myself regularly ruining my proxy & target history in Burp from opening up multitudes of tabs (even in container tabs, because I’m only human). Only logging requests from target scopes is not always helpful, as I often want to see all requests coming from an application (and not just through devtools). It turns out there is another Firefox plugin that can switch proxy traffic based on container – Container Proxy.
One thing to note is that Pwnfox doesn’t create its own containers automatically, so when you initially open it make sure to open a container for each colour, and then you’ll be able to see the PwnFox-* containers in the Container Proxy settings page. I personally like proxy’ing all Pwnfox containers through to Burp.
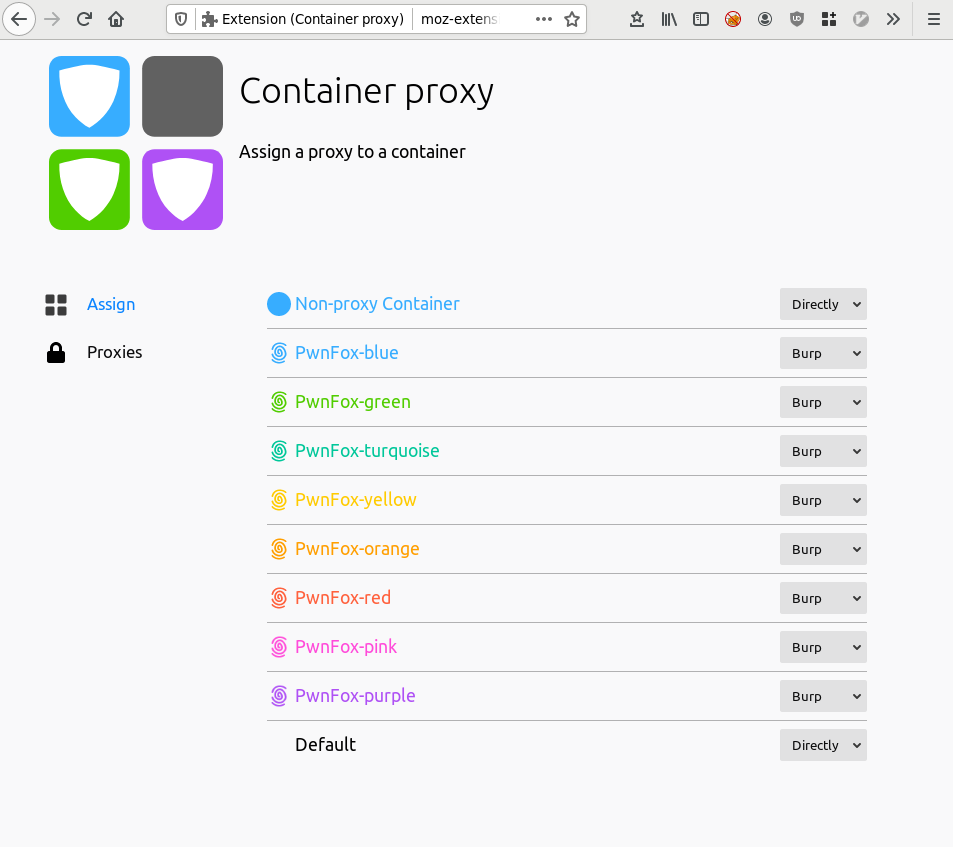
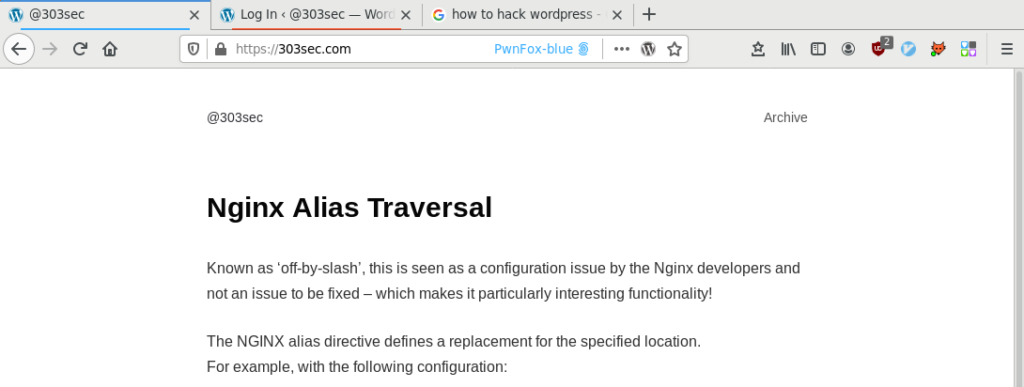
Once you have it all setup, which will take less than five minutes, the end result should look something like this on the browser:
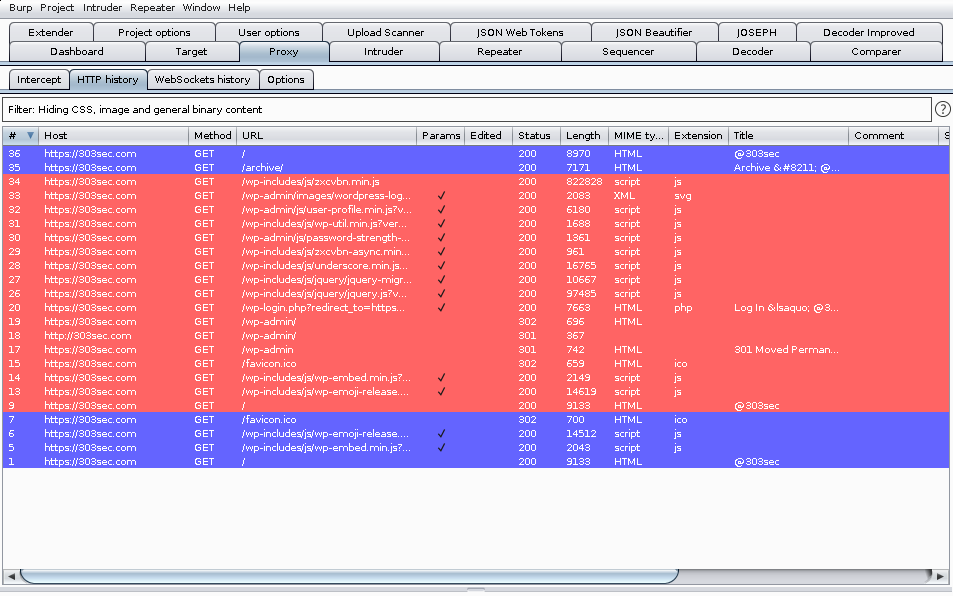
And in Burp Suite, you’ll get this:
This has made my webapp testing much more efficient and saved me many hours of frustration, so thank you to the authors of these tools for making this workflow possible.